What Is Cryptography? Everything You Want To Know
What Is Cryptography? Everything You Want To Know will be described in this article. Secret messages have been concealed and safeguarded using cryptography for thousands of years. Today’s digital world relies on cryptography to protect data and conversations as they move across the internet. Find out about cryptography and how it protects data on the internet. Install a VPN after that to enjoy unwavering privacy and automatic encryption every time you log on.
What Is Cryptography? Everything You Want To Know
In this article, you can know about What Is Cryptography here are the details below;
What is cryptocurrency?
Using mathematical principles and rules to safeguard data and communications is known as cryptography. The word “cryptography,” which comes from the Greek word “kryptos,” meaning “hidden,” is defined as the process of turning readable material into unreadable text and vice versa. Only the sender and intended recipient of a communication may see its decoded contents thanks to cryptographic technology.
Types of cryptography
The kinds of cryptographic methods that each style of cryptography uses to jumble data allow them to be identified from one another. The majority of cryptography techniques use keys, or algorithms, to encode and decode data.
The various forms of cryptography are as follows:
- Secret Key Cryptography: The data is encrypted and decrypted using a secret key. The coded message is delivered to the target recipient with the sender including the secret key. The provided key decodes the contents of the communication in the event that it is intercepted.
- Public Key Cryptography: The communication is encrypted by the sender using a public key, and it is translated by the recipient using a private key. Without the private key, it is impossible to decode the contents of an intercepted message.
- Keys are not necessary for hash functions to operate. Rather, they jumble data points of different sizes into uniformly long numbers. A one-word message and a thousand-page novel both produce a fixed-sized output of encoded text (called a hash value) when using hash algorithms, making it practically impossible to decipher the original content. Hashing is frequently used for authentication, and the MD5 hashing technique is frequently utilized.
How does cryptography work?
In order to create ciphertext—an output that can only be deciphered by the intended recipient—plaintext, also known as cleartext, is first scrambled. The data should be unintelligible to everyone other than the intended recipient because it is encoded.
The most common use of encryption in cybersecurity is to convert plaintext into ciphertext, and decryption does the opposite. The most effective encryption software makes use of complex cryptographic algorithms that are very challenging to decipher.
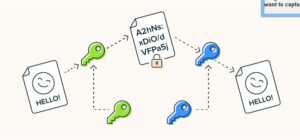
Data is encrypted and decoded using cryptography.A private key is needed to decrypt a message that has been encrypted using a public key in asymmetric encryption.
The precise method by which plaintext is transformed into ciphertext is what makes cryptography function. Some well-known encryption approaches are digital signatures, blockchain, symmetric encryption, and asymmetric encryption. Since hashing does not require keys, it is not considered encryption in the strict sense of the word. Also check Viggle Alternatives
History of Cryptography
For thousands of years, people have sent and received secret messages using codes and ciphers. The first instances of “classical” cryptography that still exist are coded hieroglyphs and cuneiform inscriptions from ancient Egypt and Babylon. These methods included substitution techniques to convert plaintext into ciphertext and vice versa.
Before the early 20th century saw the dawn of a new age in cryptography marked by more sophisticated and effective coding and decoding processes made possible by powerful electromechanical devices, these comparatively rudimentary, human cryptographic techniques remained essentially unchanged for hundreds of years.
While the development of digital computing technology hastened this trend, public-key cryptography—which makes use of distributed authentication and digital signature technologies—has advanced cryptography even further in recent years. This has made it possible for cryptography to be widely used for both personal and professional purposes, in addition to producing drastically enhanced encryption techniques.
Cryptography vs encryption
Encryption is the precise technique of turning data into code, whereas cryptography can be broadly defined as the science of conveying secret information. Although encryption is a fundamental component of cryptography, it is only one of several intricate cryptographic components required for safe information transmission. Also check Crypto IRA Platforms
Use of cryptography
Private communications and information are maintained with the use of cryptography. With cryptography, data protection reduces dangers such as ransomware assaults since information intercepted by hackers cannot be decrypted without a decryption key.
Here are some typical applications for cryptography:
- Online banking and financial transactions: To protect sensitive financial data, both online banking and e-commerce websites employ sophisticated encryption methods.
- Websites that use SSL certificates establish a secure, encrypted connection to safeguard data as it travels from your browser to the website’s server.
VPNs: A virtual personal network (VPN) encrypts the connection and reroutes online traffic to a private server.
Even if you may turn on Wi-Fi encryption in your router’s settings, if security and privacy are really vital to you, you should use a VPN. Depending on the VPN protocol being used, many VPN encryption techniques are available. For instance, the most modern VPN protocol is WireGuard, although the most widely used is probably OpenVPN.
Shop, stream, and browse the web with bank-grade encryption
When we browse the internet, our personal information is kept safe thanks to encrypted connections. With bank-grade encryption, Avast SecureLine VPN safeguards all of your online conversations and maintains the privacy of your online activities. With Avast, you can easily enable automatic encryption at the touch of a button.